|
| Recent Posts | - April, 2025-4,(1)
- January, 2025-1,(1)
- July, 2024-7,(1)
- May, 2024-5,(2)
- May, 2023-5,(1)
- February, 2023-2,(1)
- November, 2022-11,(1)
- July, 2022-7,(2)
- March, 2022-3,(1)
- November, 2021-11,(2)
- August, 2021-8,(2)
- July, 2021-7,(2)
- June, 2021-6,(1)
- May, 2021-5,(1)
- March, 2021-3,(1)
- February, 2021-2,(2)
- January, 2021-1,(7)
- December, 2020-12,(3)
- March, 2020-3,(2)
- February, 2020-2,(1)
- December, 2019-12,(2)
- November, 2019-11,(1)
- October, 2019-10,(1)
- September, 2019-9,(1)
- August, 2019-8,(1)
- May, 2019-5,(1)
- April, 2019-4,(2)
- March, 2019-3,(2)
- December, 2018-12,(1)
- November, 2018-11,(4)
- July, 2018-7,(1)
- May, 2018-5,(3)
- April, 2018-4,(2)
- February, 2018-2,(3)
- January, 2018-1,(3)
- November, 2017-11,(2)
- August, 2017-8,(1)
- June, 2017-6,(3)
- May, 2017-5,(5)
- February, 2017-2,(1)
- December, 2016-12,(1)
- October, 2016-10,(2)
- September, 2016-9,(1)
- August, 2016-8,(1)
- July, 2016-7,(1)
- March, 2016-3,(2)
- February, 2016-2,(3)
- December, 2015-12,(5)
- November, 2015-11,(5)
- September, 2015-9,(1)
- August, 2015-8,(2)
- July, 2015-7,(1)
- March, 2015-3,(2)
- February, 2015-2,(1)
- December, 2014-12,(4)
- July, 2014-7,(2)
- June, 2014-6,(2)
- May, 2014-5,(3)
- April, 2014-4,(3)
- March, 2014-3,(1)
- December, 2013-12,(2)
- November, 2013-11,(1)
- July, 2013-7,(1)
- June, 2013-6,(2)
- May, 2013-5,(1)
- March, 2013-3,(3)
- February, 2013-2,(3)
- January, 2013-1,(1)
- December, 2012-12,(3)
- November, 2012-11,(1)
- October, 2012-10,(1)
- September, 2012-9,(1)
- August, 2012-8,(1)
- July, 2012-7,(6)
- June, 2012-6,(1)
- April, 2012-4,(1)
- March, 2012-3,(3)
- February, 2012-2,(3)
- January, 2012-1,(4)
- December, 2011-12,(3)
- October, 2011-10,(3)
- September, 2011-9,(1)
- August, 2011-8,(10)
- July, 2011-7,(2)
- June, 2011-6,(7)
- March, 2011-3,(2)
- February, 2011-2,(3)
- January, 2011-1,(1)
- September, 2010-9,(1)
- August, 2010-8,(2)
- June, 2010-6,(1)
- May, 2010-5,(1)
- April, 2010-4,(3)
- March, 2010-3,(2)
- February, 2010-2,(3)
- January, 2010-1,(1)
- December, 2009-12,(3)
- November, 2009-11,(3)
- October, 2009-10,(2)
- September, 2009-9,(5)
- August, 2009-8,(3)
- July, 2009-7,(9)
- June, 2009-6,(2)
- May, 2009-5,(2)
- April, 2009-4,(9)
- March, 2009-3,(6)
- February, 2009-2,(4)
- January, 2009-1,(10)
- December, 2008-12,(5)
- November, 2008-11,(5)
- October, 2008-10,(13)
- September, 2008-9,(10)
- August, 2008-8,(7)
- July, 2008-7,(8)
- June, 2008-6,(12)
- May, 2008-5,(14)
- April, 2008-4,(12)
- March, 2008-3,(17)
- February, 2008-2,(10)
- January, 2008-1,(16)
- December, 2007-12,(6)
- November, 2007-11,(4)
|
|
|
|
Blog posts for the month of March,2008.
|
|
|
| SQL Agent - ActiveScripting subsystem failed to load | 3/31/2008 11:58:59 AM |
Began receiving alerts on a job failing. The job was "suspended". The error in the history event log is:
Unable to start execution of step 2 (reason: The ActiveScripting subsystem failed to load [see the SQLAGENT.OUT file for details]; The job has been suspended). The step failed. 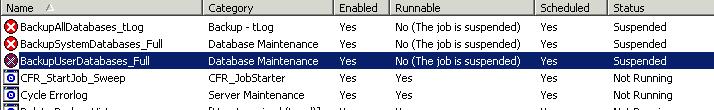
A quick review of the server shows MSDE was installed on the machine, somehow this causes an error in the registry.
Review the below registry entry and ensure there is an "s" at the end. According to Microsoft this happens sometimes with MSDE installations and upgrades. You can see the picture of mine, that it was missing
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Microsoft SQL Server\80\Tools\ClientSetup]
"SQLPath"="C:\Program Files\Microsoft SQL Server\80\Tools"

I added the "s" to the end. Started and stop the instance (i did both services because I could, but may only need to have the agent service restarted.)
Everything is working fine now.
This was on a sql server 2000 installation. |
| Outlook attachment unavailable | 3/28/2008 2:33:17 PM |
Nothing worse than an upgrade that breaks stuff. Work recently upgraded our symantec client to Symantec Endpoint Protection MR1. Great.
Next thing you know i'm getting the outlook error: 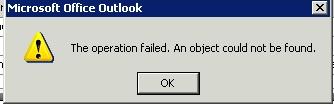
The solution was of course a patch, which is documented at:
http://service1.symantec.com/support/ent-security.nsf/854fa02b4f5013678825731a007d06af/4430b74b4f4ba805882573c60003a35c?OpenDocument
Outlook attachments are unavailable with the AntiVirus Outlook plug-in installed and disabled.
Question/Issue:
After installing Symantec Endpoint Protection MR1, Outlook attachments are unavailable with the AntiVirus Outlook plug-in installed and disabled.
Solution:
This is an issue with Symantec Endpoint Protection 11 MR1.
Symantec has created two patch files, one for 32bit operating systems and one for 64bit operating systems, to resolve this issue.
To resolve this issue without using the patch there are two steps:
- If you upgraded from Symantec Endpoint Protection 11 to Symantec Endpoint Protection 11 MR1 then you will need to disable the Outlook plug-in both in Symantec Endpoint Protection and in Outlook.
To disable the plug-in from the Symantec Endpoint Protection Manager (SEPM):
- Open up the AV policy in SEPM.
- Click on Microsoft Outlook Auto-Protect
- Unselect Enable Microsoft Outlook Auto-Protect
To disable the plug-in from within the Symantec Endpoint Protection (SEP) client interface:
- Open up the SEP client UI.
- On the AV bar, click Options and then click Change Settings...
- Click on Outlook Auto-Protect
- Unselect Enable Microsoft Outlook Auto-Protect
To disable the plug-in from Outlook:
- Open Outlook
- Click Tools -> Options
- Select the Other tab
- Click the Advanced Options button
- Click the Add-in Manager button
- Unselect the Symantec AntiVirus Outlook Protection
- If you installed Symantec Endpoint Protection 11 MR1 directly without upgrading from Symantec Endpoint Protection 11 and the above steps do not work, you will need to go to "Add or Remove Programs" to remove the AntiVirus Outlook Plug-in.
Steps to uninstall the Outlook Plug-in:
- Open up the Control Panel
- Open Add or Remove Programs
- Select Symantec Endpoint Protection
- Click Change
- When the installer comes up click Next
- Select the Modify option and click Next
- Open the AntiVirus Email Protection
- Click on the Outlook Scanner and select the This feature will not be available option
- Click Next and then Finish
|
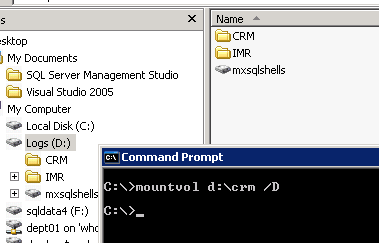
| Manually Remove a Mount Point | 3/25/2008 2:30:38 PM |
Don't ask me why, but the Mount Point failed unmounting via gui.
No error, no message, but the mount point still shows in explorer. Reboot, still shows in explorer.
Drop to the command line and run
MountVol
MountVol d:\crm /D
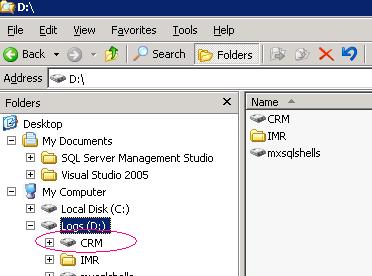
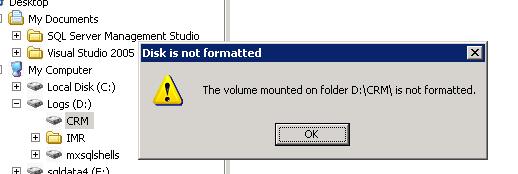
 |
| MSDE to SQL Express | 3/24/2008 1:04:50 PM |
Recently I had to evaluate a migration from MSDE to SQL Express. Always being proponent of staying on a current and supported DBMS, you might be surprised that my recommendation was to stay with MSDE.
Given that SQL Server Express 2008 is being ready for release, it does not seem prudent to migrate to SQL Server Express 2005. It may be better to use a leap frog strategy and skip SQL Express 2005, moving right to sql express 2008.
There is no doubt that SQL Express is better than MSDE, but for us, we really don't need any of the features of SQL Express, MSDE is adequate. But we do need to be on a supported DBMS that runs on Vista, and it is what is driving the upgrade. |
| Polyserve Pan Pulse Error | 3/21/2008 12:46:15 PM |
We have been experiencing a Polyserve Pan Pulse error that was difficult to troubleshoot and explain. Most perplexing was the lack of failover, as the Matrix eventlog entry for the sql instance, indicates it stopped communicating than started communicating, almost like a "stutter".
Had we not been carefully monitoring the sql instances, we would not even notice this happens, as the sql instance does not fail over, it is stopped and started by the cluster software. We run a sql agent starting job that sends an alert whenever the agent stops and starts, which alerts us to this condition.
For some reason this is only happenning on 3 of our newer machines, all DL585's 4-way dual core and a DL580 4-way quad-core machines.
The event log entries are as follow, notice they are 2 seconds apart:
--------------------------------------------
Event Type: Information
Event Source: PANPulse
Event Category: Interface
Event ID: 100
Date: 3/13/2008
Time: 1:21:26 PM
User: N/A
Computer: BCPLYSQL07
Description:
10.10.50.48 2008-03-13 13:21:26 Interface 10.10.50.48 address 10.10.50.48 has gone down
-------------------------------------------------------
Event Type: Information
Event Source: PANPulse
Event Category: Interface
Event ID: 100
Date: 3/13/2008
Time: 1:21:28 PM
User: N/A
Computer: BCPLYSQL07
Description:
10.10.50.48 2008-03-13 13:21:28 Interface 10.10.50.48 address 10.10.50.48 has come up because interface statistics indicate there is incoming traffic
-----------------------------------------------------------
What we stumbled across when reviewing this was Flow Control. The flow control is a nic card setting. These 3 machines were all set to Auto. There is an option in the HP Network Configuration Utility where you can select the Information; and it shows the currently selected Flow Control, of which all 3 of these were somehow auto-selecting Rx Pause. We reconfigured this property to disabled.
We're hoping this resolves the issue, as we couldn't understand why a sql instance would go up and down with a pan pulse error.
We have 9 servers clustered together and run SQL Instances on all of them. We only experienced the pan pulse error on these 3 machines, and all of them had the wrong flow control. |
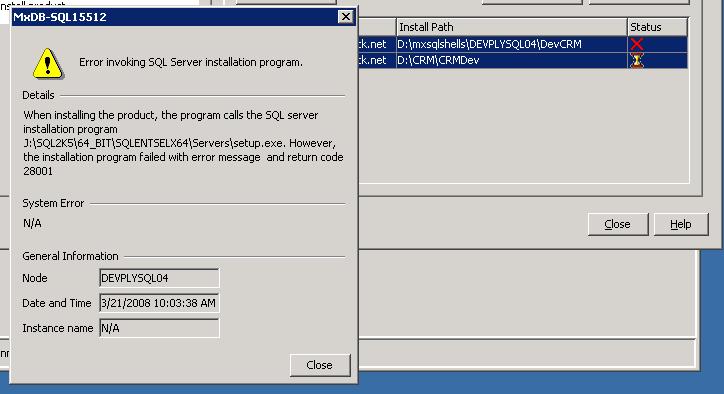
| SQL Server install fails 28001 | 3/21/2008 10:33:11 AM |
When installing SQL Server 2005 with Polyserve, the install fails with error 28001.
This is because when Polyserve first began supporting SQL Server 2005, the software had an issue / bug with the Password validation. SQL Authentication password validation did not work under Polyserve. The bug has since been fixed. But our installation uses the template.ini, which contains an sa password that does not meet the validation. So now that the bug is fixed, and password validation is working; the install fails. Solution is very simple, to edit the template.ini file to contain a password that meets the validation requirements.
To dig down into the 28001 error you have to to the individual server(s) where the install failed and find the install log file, c:\Program Files\Microsoft SQL Server\90\Setup Bootstrap\LOG\Summary.txt
|
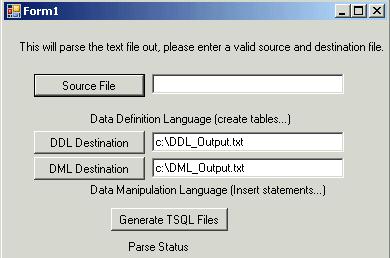
| MySQL Dump File to SQL Server | 3/13/2008 10:23:30 AM |
MySQL Dump File to SQL Server. Some how I thought this would be easy, while it was not overly difficult it did require some basic skills, parsing. I ended up not taking this as far as I wanted, but all i needed was a down and dirty import of a mysql dump file into sql server. There are many ways to do this, the best two options are to (purchase a utility) or (install mysql, import the dump file, create a proper export that sql server can read and/or an ssis package). I didn't want to install mysql or purchase a utility.
I wrote a c# program that parses the dump file out into a DDL and DML File. I than took the DDL File imported it into Erwin as a mysql database, than changed the database to SQL Server and forward engineered the schema to a TSQL Script file. I then created a SQL Server database off of the TSQL Script file. Next I ran the TSQL DML File against the database, and poof, i'm done.
This example will not work for every mysql dump file, nor did i perform lots of testing, i just needed something converted. It is not pretty code. But maybe it can help you...
There was some interesting bits in here; reversing a string, parsing a file one byte at a time and evaluating the byte, word breaking analysis and word grouping.
The resulting files still needed a little cleanup, but it was very easy. The DDL File had one data type that erwin didn't recognize. The dml file has some extraneous data from the parse, but it is easily removed.
I've included examples of the source dump file i used, and the resulting ddl and dml files.
DDL_Output.txt (2.8 KB)
mysql_dump.txt (121.02 KB)
DML_Output.txt (207.73 KB)
|
| Determining IP Address of Network Adapter | 3/20/2008 10:35:09 AM |
How do you determine which IP Address is bound to which NIC card in a mult-honed machine ?
Recently I ran into the task of ensuring the nic cards on our Clustered machines were all named with the standard "Private" and "Public" as opposed to various things like "network adapter 1" etc.
All our Private nics in the cluster start with 192.x.x.x. So to ensure I was naming them properly I needed to find what IP address was bound to "network adpater 1" etc. This seems easy but for some reason took me a while to figure this out.
( and if you look carefully in this example you will see the current nic card labeled "admin" has a public IP Address, someone goofed ! and reversed them, so this is important stuff to know how to check !)
We found two ways to do this, through windows control panel, and through our vendor's nic card configuration utility (HP).
Select Start -> Control Panel -> Network -> {Adapter Name} than right click and select status.

From the Status properties window you can select the "advanced" tab and determine which IP Address is bound to this adapter.
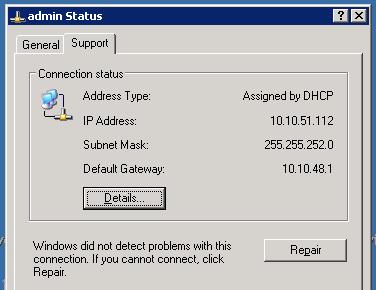
Our particular Vendor is HP, and from the HP Network Utility you can select a NIC Card and then choose, Information, and in the Details section you can find the IP Address.
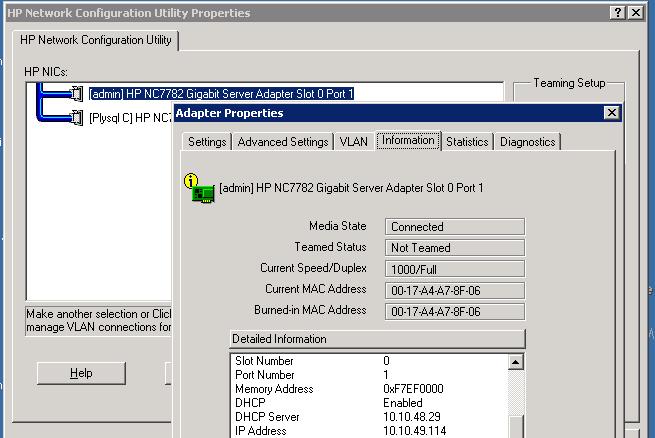
|
| Oracle Linked Server openQuery Syntax with Datefields | 3/17/2008 1:34:08 PM |
SQL Server 2005 to Oracle via Linked Server - OpenQuery Syntax with Datefields
For some reason the Oracle Linked Server in SQL Server 2005 is more "type sensitive" when it comes to data types. We've had to resort to using OpenQuery instead of the 4 part linked server syntax and using conversions of the datatypes. The unique part of using openquery is to get as much of the query to resolve on the host (oracle) side as possible, to do this you will need to become familiar with Oracle's functions
Between on two hard coded date fields:
Select * from openquery(TSR,'SELECT to_char(FILE_SEQ_ID) as FILE_SEQ_ID, MACHINE_NM, TO_CHAR(PATH_ID) AS PATH_ID, TUNER_ID, FILE_NM, TO_CHAR(FILE_SUFFIX_ID) AS FILE_SUFFIX_ID, TO_CHAR(PREVIOUS_FILE_SEQ_ID) AS PREVIOUS_FILE_SEQ_ID, LEAP_RECV_TS, CRE_PROC_TS, TO_CHAR(FILE_SOURCE_CD) AS FILE_SOURCE_CD from TSR1.LOAD_FILE_HIST where CRE_PROC_TS between to_date(''03/10/2008 03:00:00'',''mm/dd/yyyy hh24:mi:ss'') and to_date(''03/14/2008 03:30:00'',''mm/dd/yyyy hh24:mi:ss'')')
Between on hard coded date field with System Date.
Select @fin_Current = fintotal from openquery(FIN,'select SUM(tot_returns) as fintotal from division_vol_sum where sum_dttm between to_date(''01/01/2008 00:00:00'',''mm/dd/yyyy hh24:mi:ss'') and trunc(sysdate) and division_dept_id <> 24718')
|
| 256 LUNS on one FA Channel | 3/14/2008 9:34:09 AM |
We use an EMC Symmetrix SAN. We zone lots of storage. Recently had some new storage zoned and we could not "see" the storage. Turns out that 64 bit windows can only see the first 256 luns zoned to an FA Channel. Now 32 bit windows does not have this issue, so things actually "took a step backwards" with 64 bit.
This was a frustrating development. Currently we have no solution from Microsoft (thankyou). The work around is to have our SAN Administrator zone luns over 256 down another FA Channel.
Plan you SAN Carefully.
Found this:
310072 Adding support for more than eight LUNs in Windows Server 2003 and in Windows 2000
http://support.microsoft.com/default.aspx?scid=kb;EN-US;310072 |
| Polyserve login failed error 405 | 3/13/2008 2:59:09 PM |
This error is annoying. No idea why it happens, not sure if netbackup or anti-virus locks up and or corrupts the polyserve password file. So far we opened a support case, but if I remember correctly you have to reboot the server to correct this error. Fortunately you can use the matrix console from other machines, so it can wait, but very annoying.
The solution of rebooting the server worked, so this indicates to me that the file was not corrupt but some type of "permission denied" happenned. Almost as though this server did not get a "clean reboot" as both times I remember getting this error was right after a reboot or power cycle of the machine.
Related entry in the Matrix event log:
Event Type: Failure Audit
Event Source: ClusterPulse
Event Category: MxConsole
Event ID: 100
Date: 3/13/2008
Time: 2:54:20 PM
User: N/A
Computer: DEVPLYSQL02
Description:
10.10.49.162 2008-03-13 14:54:20 FailureEventAudit - user 'admin' at <10.10.49.162:3201>: failed authentication, Sys_error(C:\PROGRA~1\POLYSE~1\MATRIX~1\conf\mx_passwd: Permission denied)
Screen shot of the error:
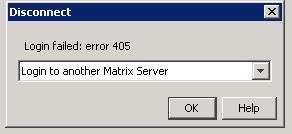
|
| CD ROM burns up motherboard / system board ! | 3/10/2008 9:20:37 AM |
Recently had an issue with a friends machine, completely dead / unresponsive. Regular troubleshooting steps yield no real reason why the machine would be in such a state, but it is 4 years old and based on the amount of hair, dust and tobacco smoke found in the machine, it's a wonder it ran this long, "Buddy, buy a new machine, it's not worth fixing".
I acquire another brick in my basement.
Two or three weeks go by, I find I need a cd drive for a test machine I have, remembering the brick, I scavenge the cd-rom and start the machine up, nothing ! Crap, i've just burned up my own test machine ! Sure enough, now I have two complete bricks, and the test machine was running fine before I put in the cd rom from the other machine. Never have I seen a cd rom fry a system board, but it has to be the root cause.
Be careful of used parts, you get what you pay for. You can bet both these bricks are going to the recycling center asap !
In attempting to fix my test machine I had to troubleshoot the system board and put together this list. It didn't help me, but was interesting to research:
AMI BIOS
Number of Beeps
None
You're supposed to hear at least one beep. If you truly don't hear anything, your computer's power supply is no good. Either that or your motherboard or PC Speaker is broken.
One
One beep is good! Everything is A-OK, that is if you see things on the screen. If you don't see anything, check your monitor and video card first. Is everything connected? If they seem fine, your motherboard has some bad chips on it. First reset the SIMM's and reboot. If it does the same thing, one of the memory chips on the motherboard are bad, and you most likely need to get another motherboard since these chips are soldered on.
Two
Your computer has memory problems. First check video. If video is working, you'll see an error message. If not, you have a parity error in your first 64K of memory. First check your SIMM's. Reseat them and reboot. If this doesn't do it, the memory chips may be bad. You can try switching the first and second banks memory chips. First banks are the memory banks that your CPU finds its first 64K of base memory in. You'll need to consult your manual to see which bank is first. If all your memory tests good, you probably need to buy another motherboard.
Three
Basically the same thing as 2 beeps. Follow that diagnosis above.
Four
Basically the same thing as 2 beeps. Follow that diagnosis above. It could also be a bad timer 1.
Five
Your motherboard is complaining. Try reseating the memory and rebooting. If that doesn't help, you should consider another motherboard. You could probably get away with just replacing the CPU, but that's not too cost-effective. Its just time to upgrade!
Six
The chip on your motherboard that controls your keyboard isn't working. First try another keyboard. If it doesn't help, reseat the chip that controls the keyboard, if it isn't soldered in. If it still beeps, replace the chip if possible. Replace the motherboard if it is soldered in.
Seven
Your CPU broke overnight. Its no good. Either replace the CPU, or buy another motherboard.
Eight
Your video card isn't working. Make sure it is seated well in the bus. If it still beeps, either the whole card is bad or the memory on it is. Best bet is to install another video card.
Nine
Your BIOS is bad. Replace the BIOS.
Ten
Your problem lies deep inside the CMOS. All chips associated with the CMOS will likely have to be replaced. Your best bet is to get a new motherboard.
Eleven
Your cache memory is bad and your computer disabled it for you. You could reactivate it by pressing -Ctrl- -Alt- -Shift-
-+- , but you probably shouldn't. Instead, replace your cache memory
Phoenix BIOS
1-1-3
Your computer can't read the configuration info stored in the CMOS. Replace the motherboard.
1-1-4
Your BIOS needs to be replaced.
1-2-1
You have a bad timer chip on the motherboard. You need a new motherboard.
1-2-2
The motherboard is bad.
1-2-3
The motherboard is bad.
1-3-1
You'll need to replace the motherboard.
1-3-3
Same as AMI BIOS 2 beeps. Replace the motherboard.
1-3-4
The motherboard is bad.
1-4-1
The motherboard is bad.
1-4-2
Some of your memory is bad.
2-_-_
Any combo of beeps after two means that some of your memory is bad, and unless you
want to get real technical, you should probably have the guys in the lab coats test the memory for you. Take it to the shop.
3-1-_
One of the chips on your motherboard is broken. You'll likely need to get another board.
3-2-4
Same as AMI BIOS 6 beeps. Keyboard controller failure.
3-3-4
Your computer can't find the video card. Is it there? If so, try swapping it with another one and see if it works.
3-4-_
Your video card isn't working. You'll need to replace it.
4-2-1
There's a bad chip on the motherboard. You need to buy another board.
4-2-2
First check the keyboard for problems. If nothing, you have a bad motherboard.
4-2-3
Same as 4-2-2.
4-2-4
One of the cards is bad. Try yanking out the cards one by one to isolate the culprit. Replace the bad one. The last possibility is to buy another motherboard.
4-3-1
Replace the motherboard.
4-3-2
See 4-3-1
4-3-3
See 4-3-1
4-3-4
Time of day clock failure. Try running the setup program that comes with the computer. Check the date and time. If that doesn't work, replace the battery. If that doesn't work, replace the power supply. You may have to replace the motherboard, but that is rare.
4-4-1
Your serial ports are acting up. Reseat, or replace, the I/O card. If the I/O is on the motherboard itself, disable them with a jumper (consult your manual to know which one) and then add an I/O card.
4-4-2
See 4-4-1
4-4-3
You math coprocessor is cussing. Run a test program to double-check it. If it is indeed bad, disable it, or replace it. Disabling is fine, because you probably don't need it anyway.
|
| Add Remove Programs not displaying | 3/7/2008 10:01:09 AM |
While trying to remove Polyserve Hotfix 4, i've consistently run into a problem with the add remove programs not displaying any programs.
Polyserve Hotfix 4 must be removed before applying hotfix 5. Open up Control Panel, Add / Remove Programs, and nothing. The list just never populates. Reboot, Reboot, nothing. Out of frustration I know the uninstall is just a program, so I search the registry for the uninstall string, cut and paste that out, and run it from the command line. See Picture below for registry, not sure if the guid is the same for all installations, so always check. The string I ran was:
MsiExec.exe /I{6D67BBA1-ECB3-4FBF-80A3-A3A34F57CE89}
Worked well, I still have no idea why the list won't populate, but I've had this issue on several windows 2003, 64 bit, sp2 machines running polyserve. It makes applying a hotfix frustrating.
The Add or Remove Programs screen never populates.
Registry entry which shows string to run to uninstall, UninstallString.
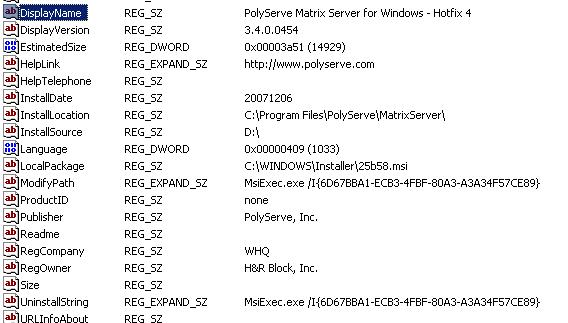
|
| Risk Reward Analysis | 3/5/2008 9:36:28 AM |
Fatally False Positives, and risk reward analysis.
I Ran across this article in National Geographic Adventure, March 2008, Deep Survival Series, by Laurence Gonzales. I read it, and just kept popping back into my mind, so I repost here, so it won't go away.
The are many points and analogies, wheather it is investing in Yahoo (past performance is not an indicator of future success), Driving a 69 VW Micro Bus or some other behavior, re-think your thought process:
------------------------------
FATALLY FALSE POSITIVES
By Contributing Editor Laurence Gonzales, author of the book Deep Survival
On December 6, 1988, Todd Frankiewicz was on Tincan Mountain in Alaska, making his comeback as a top-notch skier. The previous summer, a serious auto accident had left him hospitalized, and after months of rehabilitation, he felt ready. The day before, he had gone to city hall for a license to marry his girlfriend of nine years, Jenny Zimmerman.
That weekend the Anchorage Daily News ran headlines warning of avalanches. But Frankiewicz had skied Turnagain Pass before and took reasonable precautions, first discussing the danger with Zimmerman and then calling Doug Fesler, a friend and one of the top avalanche experts in the area. As Fesler’s wife, Jill Fredston, wrote in Snowstruck: In the Grip of Avalanches, “Todd asked careful, intelligent questions.” Significantly, “he’d never before phoned us at home to ask for a personal update.” Fesler told him to “avoid steep north-facing slopes like the plague.”
It was a gorgeous day, and the mountains were heavy with new powder. As friends came and went on the slopes, Frankiewicz skied in a party atmosphere that fit his mood. He was back. Various skiers tested slopes that looked as if they might avalanche by skiing the tops first, but the snow held. Unconsciously, they were building up a store of experience that would serve as their model for future decisions. The unconscious rule of decision-making is that the past equals the future, and that we tend to do what we’ve been rewarded for doing. Skiing provides a powerful emotional reward. Moreover, the common psychological effect called “confirmation bias” dictates that we will take any sort of evidence as proof of what we already believe.
As the day drew to a close, Frankiewicz and friends decided to climb higher on the mountain for one last, long run down the North Bowl. While that was exactly the sort of slope his friend Fesler had warned him to avoid, the accumulation of evidence and experience throughout the day had gradually widened the definition of an acceptable slope. As they started up, however, one of the skiers had a bad feeling about it and decided to descend. But for Frankiewicz, the lure of a long and triumphant final run easily offset the attention he might have paid to that ominous signal.
The fact was, the signs that would have given rise to a bad feeling were everywhere. The texture, slope angle, shape, wind markings, and structure of the snow were easy to read and test. Simply poking a ski pole through the surface would have revealed that the new snow sat as a consolidated slab on top of a rotten foundation. Everyone who knew Frankiewicz was aware that he had the knowledge and experience to have avoided the accident that followed. Or as Fredston put it, “Todd might as well have stepped in front of a bus.”
Frankiewicz skied just 20 feet down the North Bowl and cut across the slope to test its stability, figuring that if it fractured, it would drop off below him. When he came to a stop, all looked good. He called to one of his friends, Regan Brudie, who skied down to Frankiewicz. When the two were a few feet apart, “the fracture line unzipped the mountain,” to use Fredston’s words. Within seconds, Frankiewicz was dead, while Brudie was swept away, miraculously unhurt. The following day, Jenny Zimmerman left city hall “with her marriage license in one hand and her fiancé’s death certificate in the other.”
As Fredstone wrote to me recently, “It’s amazing, really, how many times the same Todd Frankiewicz kind of accident has happened. All that changes are the names.”
That kind of mistake—or cluster of mistakes—is just as common in our daily lives as in the mountains. Frankiewicz had been a skier and mountaineer all his life. Being stuck in a hospital for months was like having his identity taken away. His first day out, he had to reestablish himself in the world that was familiar to him. He may have had a bad feeling about the dangers at the beginning of the day, which could explain why he called Fesler for advice. Most people who are caught in avalanches are aware of the hazard beforehand. But when repeated testing failed to fracture the snow, Frankiewicz’s confirming store of experience grew. The fact that he was skiing slopes that were familiar contributed to his willingness to take risks. An amazing 71 percent of accidents that involve avalanches occur on slopes that are familiar to the victims. Being in a group with its party atmosphere would also have increased his confidence.
I used to run into similar accidents all the time when I was flying aerobatics. I can’t count the number of conversations I’ve had with fellow pilots after someone tried a low-level maneuver and it went bad. We all knew not to do it, and we all knew pilots who’d died trying. And then we’d stand around and ask: What was he thinking?
The same kinds of scenarios play out in business. The results may not be fatal, but they’re often costly. For example, reading a history of failed corporate mergers and acquisitions is like going through a history of avalanche accidents: They all know the dangers beforehand, but they go ahead anyway.
Relationships can work in much the same way. A friend years ago had just gotten out of a really bad marriage and spent several months swearing up and down that he’d never do it again. When I received the wedding invitation a few months later, I just slapped my forehead: What was he thinking?! The fact is, simply wanting to do something can often overwhelm all other considerations, unless you really take the time to analyze the situation.
The first step in avoiding this type of mistake is to be deeply aware of the channels of information, emotion, and influence that are flowing together to shape your decisions. Having a bad feeling is information. What if Frankiewicz had stopped the skier who decided to descend and asked him to explain his feelings more fully? Might someone have poked a ski pole into the snow and detected its rotten condition?
In addition, a recent success or failure is always a powerful influence on behavior. Because we are a species of ape, we behave according to what rewards us. Moreover, we have a strong motivation to recover from failure in order to regain status. Status confers access to resources and the right to reproduce. Frankiewicz’s death can be seen as arising at least in part from his drive to regain status (don’t forget the marriage license), which encouraged him to ignore important information.
Performing a risk-reward analysis can often clarify decisions. If the risk of a failed marriage is that you may have to experience heartache and an expensive divorce, you’d better think carefully. If the risk of a bad ski run is that you’ll die, you’d better think even more carefully about what you’ll gain by taking that risk. But be careful. As Christopher Burney, a prisoner at Buchenwald wrote, “Death is a word which presents no real target to the mind’s eye.” In a sense, Frankiewicz’s death was a failure of imagination. |
| TOE, Packet Loss, Blue Screen crash, CPU Synchronization | 3/4/2008 12:45:01 PM |
Want Fries with that ?
Experienced a Polyserve failover today, root cause has been very difficult to flush out.
One lucky hit was our solar winds monitor was reporting 80% packet loss on the server !
Since we are using server based fencing we wouldn't expect a crash dump. The problem is that the node is fenced (power_cycled) before the crash dump occurs. Unfortunately, there is really no way to determine the cause of the crash without a Memory.dmp. But, one of the side effects of TOE being enabled on the servers is a blue screen.
TOE, what's that ?
This stands for TCP/IP offload engine. Modern NICs have the ability to offload the processing of network transmission. This allows the CPU to focus on its other responsibilities. This feature is dependent on the OS supporting the feature. SP2 supports TOE. This is the first iteration of Windows that does so. It definitely has advantages, but we have seen some issues in other areas so turning it off may help solve the problem.
Of course like any good new technology, it doesn't always work right and the side effect of TOE is a blue screen, nice !
Review the attached KB Article on TOE from HP: TOE_KB.htm (5.76 KB)
At the same time, we're still working on issues with the CPU synchronization errors in the SQL Server error log:
The time stamp counter of CPU on scheduler id 14 is not synchronized with other CPUs.
The time stamp counter of CPU on scheduler id 2 is not synchronized with other CPUs.
See Microsoft KB Article: http://support.microsoft.com/default.aspx?scid=kb;EN-US;931279
Now this error I though only affected the AMD Chipsets, but this particular machine is an Intel 4 way quad core, so 16 processors. On the AMD Chipsets we modified a boot.ini file with /usepmtimer, but on this intel box we had to go to the bios settings.
Hopefully after changing the BIOS Power settings to maximum always, we'll see no more fail overs and no more synchronization issues. 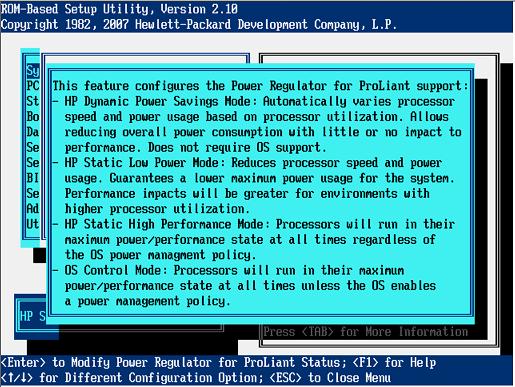 |
| Grant Truncate Table Permissions in SQL Server ? | 3/3/2008 3:24:36 PM |
This has been a thorn in my side as long as I have worked with SQL Server. There are times you want to grant truncate table permissions, either on a table or all tables etc to a specific user and/or service account, BUT you do not want to grant any alter or DDL privlidges or worse db owner!
Now why Microsoft, in SQL Server 2005 did not make this available, I do not know; as smart as the people who I have seen and met that work on the product, I'm sure they could have overcome any technical issue given them. And please don't use ANSI Standard or some other weak excuse. I want to be able to type "Grant Truncate on Table to User", just like Select, Update or Delete. Too BAD for me.
Fortunately Micro$oft did give us a "fishing pole", so go learn how to fish and explore: execute as. With this procedure you can delegate and impersonate to accomplish tasks.
So the basic setup we devised, (which was based on a model used by our Oracle group):
- Stored procedure - using Execute As to elevate rights
- Control Table - to determine which tables a user is authorized to truncate
- Audit Table - who, what and when (could be enhanced for why !)
The scripts below need a slight review and may need work for you particular enviornment, but the "guts" of the process is here. Note that the control and audit table are in a dedicated DBA Schema.
USE {database}
GO
/****** Object: Schema [dba] Script Date: 03/03/2008 13:26:31 ******/
CREATE SCHEMA [dba] AUTHORIZATION [dbo]
/****** Object: Table [dba].[TRUNCATE_AUDIT] Script Date: 03/03/2008 13:26:15 ******/
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
SET ANSI_PADDING ON
GO
CREATE TABLE [dba].[TRUNCATE_AUDIT](
[Truncate_Audit_Id] [int] IDENTITY(1,1) NOT NULL,
[HostName] [varchar] (30) NOT NULL CONSTRAINT [DF__TRUNCATE___HostN__440B1D61] DEFAULT (host_name()),
[UserName] [varchar] (30) NOT NULL,
[DATETIME] [datetime] NOT NULL CONSTRAINT [DF__TRUNCATE___DATET__44FF419A] DEFAULT (getdate()),
[TABLE_NAME] [varchar] (100) NOT NULL,
[TABLE_OWNER] [varchar] (30) NOT NULL,
[SUCCESS] [int] NOT NULL CONSTRAINT [DF__TRUNCATE___SUCCE__45F365D3] DEFAULT ((-1)),
CONSTRAINT [PK__TRUNCATE_AUDIT__4316F928] PRIMARY KEY CLUSTERED
(
[Truncate_Audit_Id] ASC
) WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON) ON [PRIMARY]
) ON [PRIMARY]
GO
SET ANSI_PADDING OFF
/****** Object: Table [dbo].[TRUNCATE_LIST] Script Date: 03/03/2008 13:35:01 ******/
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
SET ANSI_PADDING ON
GO
CREATE TABLE [dba].[TRUNCATE_LIST](
[List_Id] [int] IDENTITY(1,1) NOT NULL,
[List_Table_Name] [varchar] (256) NOT NULL,
CONSTRAINT [PK_dba.TRUNCATE_LIST] PRIMARY KEY CLUSTERED
(
[List_Id] ASC
) WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON) ON [PRIMARY]
) ON [PRIMARY]
GO
SET ANSI_PADDING OFF
/****** Object: StoredProcedure [dbo].[TRUNCATE_TBL] Script Date: 03/03/2008 13:27:22 ******/
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
USE [{database}]
GO
/****** Object: StoredProcedure [dbo].[TRUNCATE_TBL] Script Date: 03/03/2008 13:43:10 ******/
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
CREATE Procedure [dbo].[TRUNCATE_TBL] @tbl varchar(1000),@owner varchar(30)='dbo'
WITH EXECUTE AS SELF
as
begin
Declare @username varchar(30)
Set @username = Original_login()
If exists (select * from dba.truncate_list
Where [List_Table_Name] = @tbl)
Begin
Declare @rc int
Declare @truncate_Audit_id int
Insert into dba.truncate_Audit (table_name,table_owner,username)
Values (@tbl,@owner,@userName)
Set @truncate_audit_id = scope_identity()
declare @dynamic_sql nvarchar(1000)
set @dynamic_sql = 'Truncate Table ' + @owner + '.' + @tbl
--Print @dynamic_sql
set @rc = -1
BEGIN TRY
exec @rc = sp_executeSQL @dynamic_SQL
END TRY
BEGIN CATCH
DECLARE @ErrorMessage NVARCHAR(4000),
@ErrorNumber INT,
@ErrorSeverity INT,
@ErrorState INT,
@ErrorLine INT,
@ErrorProcedure NVARCHAR(200);
SELECT @ErrorNumber = ERROR_NUMBER(),
@ErrorSeverity = ERROR_SEVERITY(),
@ErrorState = ERROR_STATE(),
@ErrorLine = ERROR_LINE(),
@ErrorProcedure = ISNULL(ERROR_PROCEDURE(), '-');
SELECT @ErrorMessage =
N 'Error %d, Level %d, State %d, Procedure %s, Line %d, ' +
'Message: '+ ERROR_MESSAGE();
-- Raise an error: msg_str parameter of RAISERROR will contain
-- the original error information.
RAISERROR (@ErrorMessage,@ErrorSeverity,1,
@ErrorNumber ,@ErrorSeverity,@ErrorState,@ErrorProcedure,
@ErrorLine )
RETURN @RC
END CATCH
Update dba.truncate_audit
Set success = @rc
Where truncate_audit_id = @truncate_audit_id
End
ELSE
Begin
RAISERROR('Cannot find the object because it does not exist or you do not have permissions.',
16 ,1,1088,16,7,'[dbo].[TRUNCATE_TBL]',1)
Return -1
End
END
/*
Insert into dba.truncate_list values ('DW_List')
Insert into dba.truncate_list values ('Daily_Efile')
grant exec on dbo.truncate_tbl to leap_efile_dw_pull_dev
grant exec on dbo.truncate_tbl to [hrbinc\x104041]
create table dbo.bob (col1 char(10))
-- drop table bob
*/
/*
insert into bob values ('test1')
insert into bob values ('test2')
insert into bob values ('test3')
insert into bob values ('test4')
truncate table dba.truncate_list
*/ |
| SOX Compliance and the database, missing the target ! | 3/3/2008 11:06:19 AM |
SOX Compliance has missed the target.
I work a lot lately with auditors and sox compliance, and I wonder if this is just something that got created to drum up business. Post Entron, SOX was supposed to restore confidence, I highly doubt Enron's balance sheet was corrupted by lax database standards. It's always good to have a good security policy in place, but it seems that SOX Compliance and database security while on parrallell paths diverge when it comes to intent.
A recent article about how companies still "hide" (really under-report) off-balance sheet liabilities, show how SOX has missed the target. Reading this article than made me think, about why as DBA's we spend so much time on SOX Compliance, when the real issue has very little to do with IT standards. Not that IT standards and security are not important, but when it comes to SOX, maybe these audit companies are spending too much time looking at the wrong department.
The original article is located here:
http://www.iht.com/articles/2008/02/28/business/norris29.php
FLOYD NORRIS
Off-the-balance-sheet mysteries
Should we blame the accountants? Surprises multiplied as the subprime problem of 2007 grew into the credit crunch of 2008.
It is one thing to have a bank report losses because some of the loans on its balance sheet went bad. That is part of the business of banking. It is something else, however, for a bank to report a multi-billion dollar loss from taking some risk that had never been mentioned in its financial statements.
Haven't we seen this movie before, involving a company called Enron? Didn't Congress pass a law requiring that the problem of the off-the-balance sheet mysteries be solved?
"After Enron, with Sarbanes-Oxley, we tried legislatively to make it clear that there has to be some transparency with regard to off-balance-sheet entities," Senator Jack Reed of Rhode Island, the chairman of the Senate Securities subcommittee, said this week. "We thought that was already corrected and the rules were clear and we would not be discovering new things every day."
Reed, a Democrat, has sent letters to the Securities and Exchange Commission, as well as to the Financial Accounting Standards Board, which sets U.S. accounting rules, and the International Accounting Standards Board, which does the same for most of the rest of the world. He is asking detailed questions about what went wrong and how it should be fixed.
One rule that needs scrutiny now - called 46-R - was passed after Enron. Essentially, it says that companies can keep "variable special purpose entities" off their balance sheets if they conclude that the bulk of the rewards, and risks, lie with others.
Suddenly, losses are booked. Investors learn that a company has taken a risk only after the risk has gone bad.
That should not happen. The rules require that companies make some disclosures about vehicles off their balance sheets, even if they do not put them on their financial statements.
But those disclosures have often not been made, or have been made in such a general way as to be meaningless. The SEC, and perhaps the Congress, should ask some companies to explain their earlier lack of disclosures.
They will hear that companies thought the amounts involved were unimportant - "not material" in the jargon of accounting. They may find out that some managements did not understand all the risks that were being taken. And they may find that some companies failed to disclose risks that they should have disclosed.
The 2007 annual report of State Street Corp., a Boston bank, is a model of what disclosures should be, in laying out the risks of some special purpose entities it set up to hold assets. Those entities, known as conduits, borrowed money to pay for the assets, with State Street promising to come up with the cash if the conduits could not find other lenders.
In the report, State Street explains why it has not taken any write-off on those conduits, which contain $28.8 billion in what the bank believes to be high quality assets.
It can avoid consolidation because other investors would suffer the first $32 million of losses - about one-tenth of one percent of the assets. After that State Street would be on the hook. But State Street says its model indicates that defaults on the underlying assets will not cost that much.
So long as the conduits stay off State Street's balance sheets, it does not have to adjust them to reflect the market value of the assets in the conduits. But if State Street ever concludes that defaults are likely to be a little higher - say $100 million, an amount that is only 3 tenths of a percent of assets - then it would have to put the assets on its balance sheet. And if it did that, it would have to write them down to market value.
At the end of last year, State Street estimates that market value was about $850 million below face value. Had it been forced to consolidate the conduits, that loss would have been posted, leaving a write-down of about $530 million after taxes. About 40 percent of the bank's 2007 profits would have vanished.
|
|
Blog Home
|
|
|
|